5.57. calendar
| DESCRIPTION | LINKS |
- Origin
- Constraint
- Type
- Arguments
- Restrictions
- Purpose
Makes the link between an universal calendar and resource dependent calendars. Given a collection of machines where each machine is defined by its identifier and its unavailability periods the constraint maps items of real and virtual dates depending on the machine assignment as well as of the fact that we consider start () or end () times. Virtual dates on a given machine do not consider the unavailability periods on , while real dates consider all time points.
- Example
-
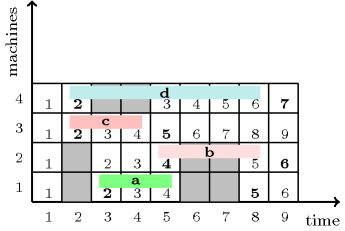
Figure 5.57.1 illustrates the example. It present four machines with their respective unavailability periods (in grey) as well as four tasks (in blue and pink). Each item of the collection corresponds to the start or to the end of one of the previous four tasks. The constraint holds since:
The real date 3 () associated with the start () of task (a) in the universal time corresponds to the virtual date 2 () on machine 1 ().
The real date 6 () associated with the end () of task (a) in the universal time corresponds to the virtual date 5 () on machine 1 ().
The real date 5 () associated with the start () of task (b) in the universal time corresponds to the virtual date 4 () on machine 2 ().
The real date 9 () associated with the end () of task (b) in the universal time corresponds to the virtual date 6 () on machine 2 ().
The real date 2 () associated with the start () of task (c) in the universal time corresponds to the virtual date 2 () on machine 3 ().
The real date 5 () associated with the end () of task (c) in the universal time corresponds to the virtual date 5 () on machine 3 ().
The real date 2 () associated with the start () of task (d) in the universal time corresponds to the virtual date 2 () on machine 4 ().
The real date 9 () associated with the end () of task (d) in the universal time corresponds to the virtual date 7 () on machine 4 ().
Figure 5.57.1. Four machines with their unavailability periods as well as four tasks assigned to these machines (virtual dates mentioned in the Example slot use a bold font)
- Typical
- Symmetries
Items of are permutable.
Items of are permutable.
- Arg. properties
Contractible wrt. .
- Usage
The constraint is used as a channelling constraint in resource scheduling problems where resources have unavailability periods that can preempt the execution of a task. In this context two time coordinates systems are used:
A first coordinate system, so called the virtual coordinate system, ignores all unavailability periods on the different resources. All resource constraints are stated within this virtual coordinate system.
A second coordinate system, so called the real coordinate system, corresponds to the real time. All temporal constraints (e.g., precedence constraints) are stated within this real coordinate system.
In this context, each task has a virtual origin, a virtual duration, a virtual end, a real origin, a real duration, a real end and the constraint links together the virtual origin and the real origin as well as the virtual end and the real end. The virtual duration (i.e., the real duration plus the sum of the unavailability periods crossed by the task) is linked to the virtual end and the virtual origin through an equality constraint on the difference between the virtual end and the virtual origin. The real duration is linked in a similar way to the real end and the real origin. The keyword scheduling with machine choice, calendars and preemption provides a concrete example of resource scheduling problem using the constraint.
- Reformulation
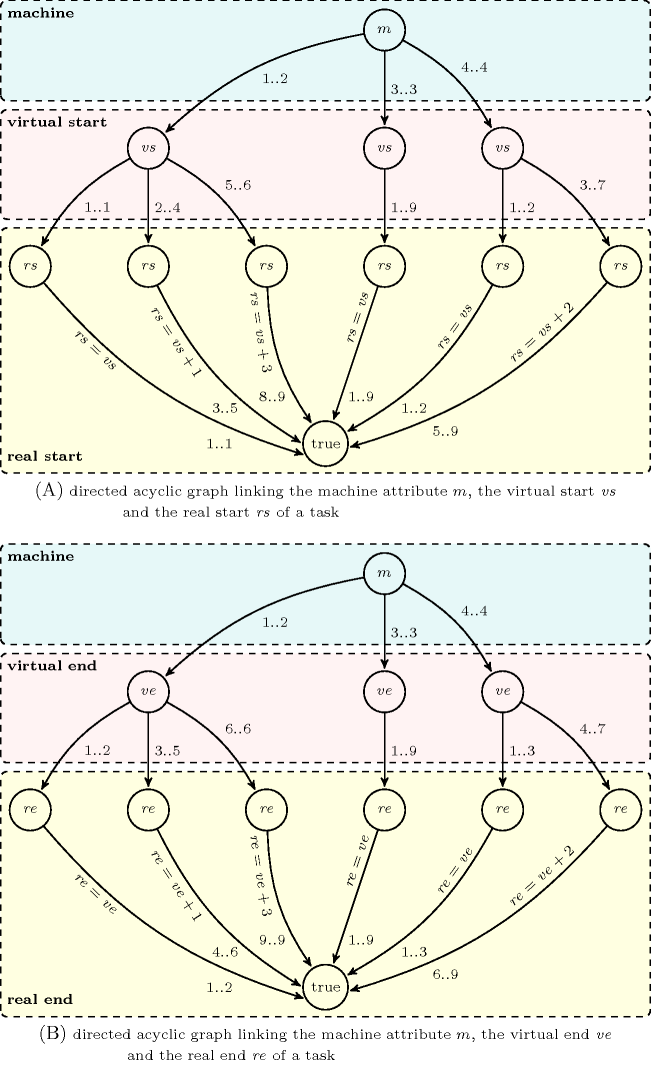
The constraint can be reformulated into two generalised constraints (i.e., two constraints augmented with linear constraints). Part (A) (respectively Part (B)) of Figure 5.57.2 provides the directed acyclic graph that allows mapping the virtual start and real start (respectively the virtual end and real end) of a task. This directed acyclic graph can be computed directly from the arguments of the constraint:
We create an initial root node labelled by and we partition the set of machines into classes of consecutive machines that all share exactly the same unavailability periods. For each such class we create an arc from the root node to a new node labelled by the corresponding interval of consecutive machines identifiers. In Part (A) this corresponds to node and its three outgoing arcs respectively labelled by intervals , and .
For each class of consecutive machines found previously, we label in increasing order each timepoint that is not part of an unavailability period. We create an arc from the corresponding node for each maximum interval of available timepoints to a new node labelled by . In Part (A) this translate to:
For the class corresponding to machines 1 and 2 we create three outgoing arcs labelled by the time intervals , and .
For the class corresponding to machine 3 we create the outgoing arc labelled by time interval .
For the class corresponding to machine 4 we create the two outgoing arcs labelled by the time intervals and .
For each class of consecutive machines and for each maximum interval of available timepoints previously computed, we find out the number of unavailable timepoints on the same class of machines that are located before the virtual date . We create an outgoing arc from the corresponding node to a new node labelled by (there is a single node for the full directed acyclic graph). This arc is labelled by the interval and by the linear constraint . In Part (A) this translate to:
For the class corresponding to machines 1 and 2 and for each node associated with the time intervals , and we respectively create an outgoing arc labelled by intervals , and . To each of these arcs we also respectively associate the linear constraints ( since on machines 1 and 2 there is no unavailability period before the virtual date 1), ( since on machines 1 and 2 there is a single unavailable timepoint before the virtual date 2) and ( since on machines 1 and 2 there is three unavailable timepoints before the virtual date 5).
For the class corresponding to machine 3 and for the node associated with the time interval we create the outgoing arc labelled by time interval and by (i.e., since their is no unavailability period at all on machine 3).
For the class corresponding to machine 4 and for each node associated with the time intervals and we respectively create an outgoing arc labelled by and . To each of these arcs we also respectively associate the linear constraints ( since on machine 4 there is no unavailability period before the virtual date 1) and ( since on machine 4 there is two unavailable timepoints before the virtual date 3).
Figure 5.57.2. The two generalised constraints for respectively mapping (A) the virtual start and real start of a task corresponding to the Example slot as well as (B) the virtual end and real end; the directed acyclic graphs were generated under the hypothesis that the virtual and real dates are located in .
The constraint can also be reformulated into a conjunction of reified constraints. This is done by generating, for each pair of items of the and collections, a set of reified constraints expressing:
The link between the real and the virtual dates under the hypothesis that the attribute of item is assigned to the value of the attribute of item . More precisely, we generate one reified constraint for each available time interval on machine .
The fact that a real date should not be located within an unavailability period of its corresponding machine.
Operationally, this leads to the following cases:
When machine has no unavailability at all we state an equality constraint between the real and virtual dates.
When the real date is located before the first unavailability period we also state an equality constraint between the real and virtual dates.
When the real date is located between two consecutive unavailability periods we state:
An equality constraint between the real date and the virtual date plus the sum of all unavailabilities located before the real date.
An implication between the fact that the real date belongs to the first unavailability period (among the two consecutive unavailability periods) and the fact that the real date is not assigned to the machine that contains the unavailability period.
When the real date is located after the last unavailability period we state:
An equality constraint between the real date and the virtual date plus the sum of all unavailabilities.
An implication between the fact that the real date belongs to the last unavailability period and the fact that the real date is not assigned to the machine that contains the unavailability period.
As an example consider again consider the instance given in the Example slot. For the start of task a (i.e., the first item of collection ), we generate the following reified constraints, where equivalences of the form are shown in bold:
(if task a is assigned on machine 1)
before :
between and :
after :
do not cross , : ,
(if task a is assigned on machine 2)
before :
between and :
after :
do not cross , : ,
(if task a is assigned on machine 3)
no unavailability:
(if task a is assigned on machine 4)
before :
after :
do not cross :
For the end of task a (i.e., the second item of collection ), we generate the following reified constraints:
(if task a is assigned on machine 1)
before :
between and :
after :
do not cross , : ,
(if task a is assigned on machine 2)
before :
between and :
after :
do not cross , : ,
(if task a is assigned on machine 3)
no unavailability:
(if task a is assigned on machine 4)
before :
after :
do not cross :
For the start of task b (i.e., the third item of collection ), we generate the following reified constraints:
(if task b is assigned on machine 1)
before :
between and :
after :
do not cross , : ,
(if task b is assigned on machine 2)
before :
between and :
after :
do not cross , : ,
(if task b is assigned on machine 3)
no unavailability:
(if task b is assigned on machine 4)
before :
after :
do not cross :
For the end of task b (i.e., the fourth item of collection ), we generate the following reified constraints:
(if task b is assigned on machine 1)
before :
between and :
after :
do not cross , : ,
(if task b is assigned on machine 2)
before :
between and :
after :
do not cross , : ,
(if task b is assigned on machine 3)
no unavailability:
(if task b is assigned on machine 4)
before :
after :
do not cross :
For the start of task c (i.e., the fifth item of collection ), we generate the following reified constraints:
(if task c is assigned on machine 1)
before :
between and :
after :
do not cross , : ,
(if task c is assigned on machine 2)
before :
between and :
after :
do not cross , : ,
(if task c is assigned on machine 3)
no unavailability:
(if task c is assigned on machine 4)
before :
after :
do not cross :
For the end of task c (i.e., the sixth item of collection ), we generate the following reified constraints:
(if task c is assigned on machine 1)
before :
between and :
after :
do not cross , : ,
(if task c is assigned on machine 2)
before :
between and :
after :
do not cross , : ,
(if task c is assigned on machine 3)
no unavailability:
(if task c is assigned on machine 4)
before :
after :
do not cross :
For the start of task d (i.e., the seventh item of collection ), we generate the following reified constraints:
(if task d is assigned on machine 1)
before :
between and :
after :
do not cross , : ,
(if task d is assigned on machine 2)
before :
between and :
after :
do not cross , : ,
(if task d is assigned on machine 3)
no unavailability:
(if task d assigned on machine 4)
before :
after :
do not cross :
For the end of task d (i.e., the eighth item of collection ), we generate the following reified constraints:
(if task d is assigned on machine 1)
before :
between and :
after :
do not cross , : ,
(if task d is assigned on machine 2)
before :
between and :
after :
do not cross , : ,
(if task d is assigned on machine 3)
no unavailability:
(if task d is assigned on machine 4)
before :
after :
do not cross :
- See also
common keyword: (scheduling constraint), (scheduling with machine choice, calendars and preemption), (multi-site employee scheduling with calendar constraints,
scheduling with machine choice, calendars and preemption), (scheduling constraint),
- Keywords
constraint type: predefined constraint, temporal constraint, scheduling constraint.
modelling: channelling constraint, multi-site employee scheduling with calendar constraints, scheduling with machine choice, calendars and preemption, assignment dimension.
modelling exercises: multi-site employee scheduling with calendar constraints, scheduling with machine choice, calendars and preemption.